ISO 27001 Certification (ISMS)
An ISO 27001 (ISMS) is a systematic process for managing delicate organisations’ information so that it remains secure.
An ISO 27001 (ISMS) particularly suitable where the protection of data is essential. For example, banking, financial, health, public and IT sectors.
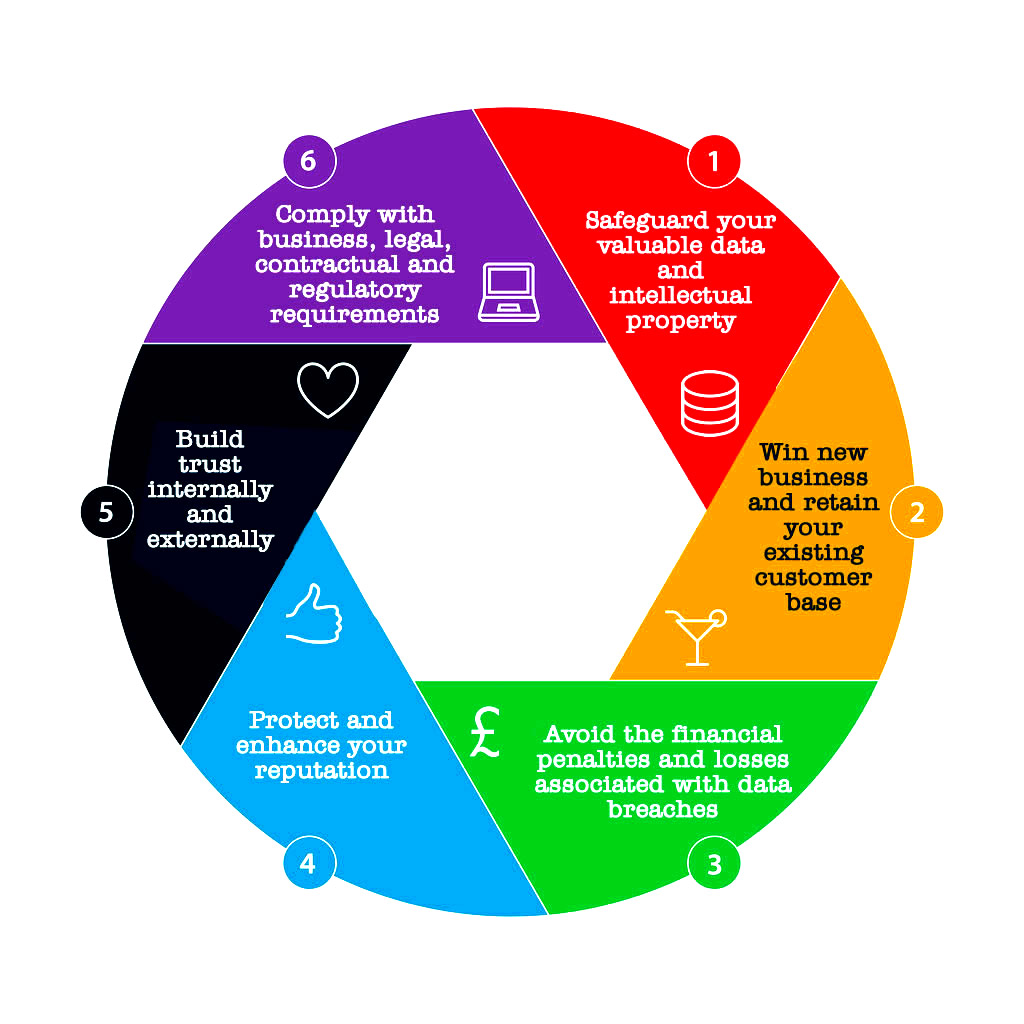
Benefits of ISO 27001 (ISMS) Certification
- Establish trustworthiness with customers, stakeholders, employees, trading partners.
- Ensure compliance with mandates and laws.
- Possibly lower rates on insurance.
- Provide competitive advantages
- Reduce cost connected with the improvement of process efficiency and the management of security costs.
- Reduces liabilities and risk due to implemented or enforced policies and procedures, which demonstrate due diligence.
What is ISO 27001 Certification Process?
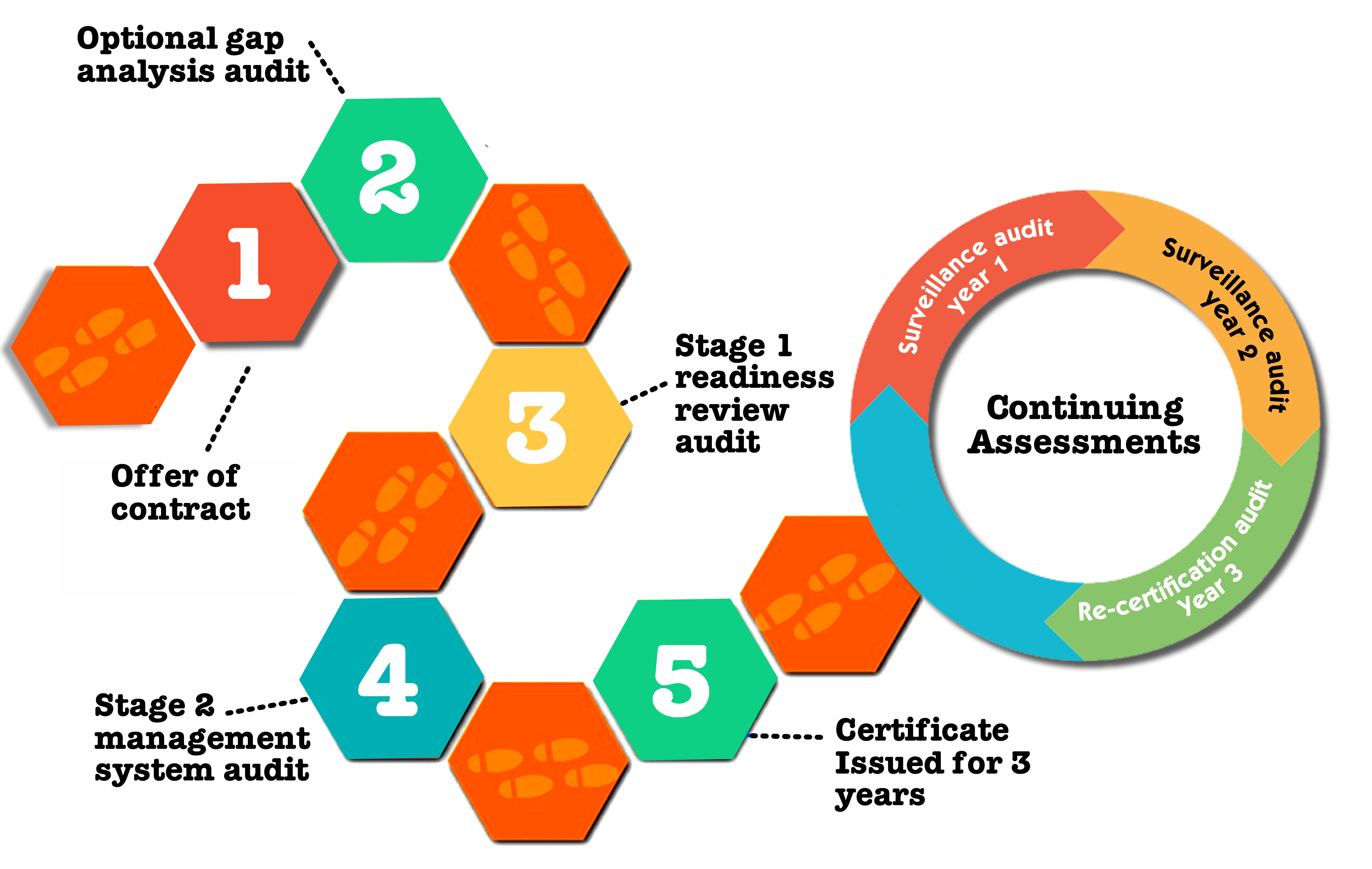
Integrated Management Systems
There are various mutual fundamentals between ISO 9001, ISO 14001, ISO 45001 and ISO 27001. E.g. Document control, management review, document control, corrective action and the requirement for competent personnel. According to Annex SL, a new high-level structure, you can combine these standards into a single joint system.
Get a free quoteAn ISO 27001 (ISMS) can help small, medium and large businesses in any sector by securing assets critical information. It is also vital for information on the hard drives of computers. ISO 27001 particularly suitable where the protection of data is essential. For example, banking, financial, health, public and IT sectors.
ISO 27001 safeguards your organisation and ensure it is adequately protected. There are many ways we use or store information. E.g. print, store electronically, post and email etc.
Risk management is an essential characteristic of the Information Security Management System. The ISO 27001 standard explicitly use the approach of assessment towards the security of assets and information. In the initial evaluation, you acknowledge the risks and then implement controls to mitigate them.
Accomplishing and sustaining ISO 27001 promises your customers, that, you realise the security of the customer’s information is vital for your organisation.
Loss of information can lead to considerable consequences. Implementing ISO 27001 cannot make your organisation resistant from security breaks. However, it will make them less probable to happen.
Benefits of ISO 27001 (ISMS) Certification
- Establish trustworthiness with customers, stakeholders, employees, trading partners.
- Ensure compliance with mandates and laws.
- Possibly lower rates on insurance.
- Provide competitive advantages
- Reduce cost connected with the improvement of process efficiency and the management of security costs.
- Reduces liabilities and risk due to implemented or enforced policies and procedures, which demonstrate due diligence.
- Aids better awareness of security throughout the organisation
- Enables organisations to avoid the possibly devastating financial losses caused by data breaches.
There are various common fundamentals between ISO 9001, ISO 14001, ISO 45001 and ISO 27001. E.g. Document control, management review, , corrective action and the requirement for competent personnel. According to Annex SL, a new high-level structure, you can combine these standards into a single joint system.
Benefits of Integrated Management Systems
- Integrated Management Systems will have a constructive impact on the outcomes of the ISO Management Systems.
- will be able to align common components of management system standards. E.g. policies, objectives, processes and resources. Also, you may be able to have a single procedure for, document control, management reviews, training, internal audits or improvements.
- Maintaining the system will become easy to understand. Therefore, there will be more focus on achieving objectives that are central to the organisation.
- Organisations will be able to have a systematic approach to changes. Therefore, decision making will be more comfortable.
- Organisations will be able to conduct integrated audits and assessments. Therefore, optimise processes and resources. And will result in less interruption and thus decrease costs.
- Resources will focus on process implementation and add value rather than additional system maintenance.
- Will require less maintenance for continuing compliance checks to ensure that you are maintaining the management system standards requirements. Therefore, there will be more focus on improvements rather than maintaining multiple systems.
What is Annex SL?
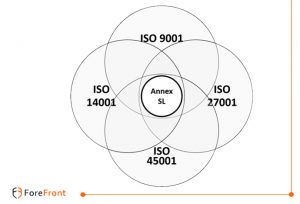
Annex SL a new high-level structure for all ISO Management System Standards in future.
Annex SL is not an ISO standard. However, it is a guide to help ISO consultants and organisations to implement multiple/integrated (MMS/IMS) Management Systems Standards. Over the years, ISO has published several management system standards for areas of quality, environment, information security, health and safety and many more. ISO management system standards share common fundamentals. However, they are not sufficiently aligned, so they were difficult to integrate at the implementation phase. The most significant disadvantage was the duplication of work. The guideline of Annex SL will help you to create a system that entails less maintenance and resources, e.g. producing one document or process instead of many.
“It is the publication of Annex SL (formerly ISO Guide 83) which outlines the framework for a generic management system. All new ISO Management System Standards (MSS) will follow to this framework, and all current MSS will migrate to the structure at their succeeding revision.
In future, all ISO Management System Standards (MSS) should be consistent and compatible - they will all have the same look and feel. Annex SL guidelines could be the commencement of the end of the conflicts, duplication, confusion and misunderstanding arising from slightly different requirements across the various ISO Management System Standards.”
Reference IRCA briefing note Annex SL
Annex SL (a high-level structure ) is created to incorporate more than one ISO standard. Several organisations seek to implement and certify multiple management system standards such as ISO 9001, ISO 14001, ISO 27001 and ISO 45001. Implementation of more than one standard has led to the necessity to combine or integrate them effectively and efficiently. Annex SL (a high-level structure ) helps the organisations to incorporate these standards. Annex SL defines the outline for a conventional ISO Management System.
The Annex SL structure and commonly used terms and definitions will make it easier to comply with and maintain the ISO standards requirements with less time and at a lower cost.
The most popular standards using Annex SL are:
- ISO 9001:2015 Quality Management System (QMS)
- ISO 14001:2015 Environmental Management System (EMS)
- ISO 27001 Information technology Management System (ISMS)
- ISO 45001:2018 Occupational Health & Safety Management System Standard (OHSMS)
At Forefront, we believe that certification should add value to your organisation. We are not merely offering a compliance audit, however, by also maintaining a commitment to impartiality, we will dedicate our expertise towards your business, so you feel your accomplishment of achieving certification means something and not just a badge on the wall.
At Forefront, we commit to fixed daily rates with no hidden fees. However, the number of days which depends on the scope (What exactly you do) and the size of the organisation (e.g. the number of employees and number of shifts and sites) are calculated according to the UKAS specified guidelines.
Cybercrime is a criminal act committed using computers and the internet.
All organisations hold accountability for the risk of theft, fraud, and should address risks by putting in place proportional controls to mitigate the risks.
Email hacking: Email hackers attempt to gain access to email accounts by tricking people into the opening and responding to spam emails, phishing emails, emails with harmful content, also known as a virus.
Phishing: Phishing messages look trustworthy with a similar format to official emails and also use corporate logos. Phishing emails request for verification of account numbers, personal information, passwords and date of birth. The people who respond to may suffer financial losses.
Malvertising: Sometimes, cybercriminals use advertisements or click on what looks like an advert as a means to hack into computers.
To mitigate the risk of above as a minimum, we should do:
- Strong passwords for all your devices and accounts.
- Use the wrong mother’s maiden name
- Use firewalls
- Antivirus software and process for systematic scanning for malware.
- Check if the email address is genuine before, for example, sending payment, data or passwords.
- Contact directly with the sender, for instance, change of bank details or requests payment.
- Communicate the risks of using public Wi-Fi.
ISO 27001 strategies for organisations
As part of its assessment evaluation organisations should consider some following examples:
- Organisations should have a clear understanding of cyber threats and their vulnerabilities. Also, the information it holds and which are critical to the business operations.
- Protect their IT devices, including hardware, software and data, from accidental or unauthorised access.
- The organisation should proactively manage cyber risks as an integrated part of comprehensive risk management by inspecting security policies, technical activities.
- The organisations should govern processes in place to safeguard and mitigate threats.
- Training and processes, for staff to protect devices and data outside formal work settings, including in transit.
- Security policies for safe use of removable media such as CDs, flash/pen drives, and mobile phones. And logs review for strange behaviour.
- Train staff about cyber risks. For example, the threat from public Wi-Fi, dangers from the use of removable media such as USB sticks, maintain backups and keep away from using personal accounts for business purposes and reporting of incidents and issues.

